What Are The Filtering Types Of Firewall?
- By john.pbtm
- •
- 13 Apr, 2017
- •

Importance Of Firewall:
The most critical component for the stable positioning of IT security of a business is firewall. Designed just like a wall for security of a physical building, the main purpose of their security is to prevent the entire connected devices from external attacks.
In a wide network, when a single device or one part of the whole network is under attack and is accessed through unauthorized means, the firewall management
is performed in such a way that it will allow the rest of devices and other parts of the network unharmed.
As individuals are continuously looking forward for observing interesting facts of technology innovations, so is the interesting facts regarding firewall protection are presented here. These facts are those agents that have given weight to the importance of firewall protection.
Firewall Types:
There are different ways in which firewall is existing to provide unbreakable continuous security. They are available either as a dedicated hardware appliance, as a managed service for security or in software form installed on a machine.
Those who have access to firewall software through the operating system they are using, like home users so that they can control themselves. Such type of firewalls gives users the authority of shutting it off altogether.
The case is a bit different in hardware appliances that are acting as a firewall. These are usually routers including a built-in network card and hub. The rest of devices and systems are connected to the router for accessing internet and each other as well.
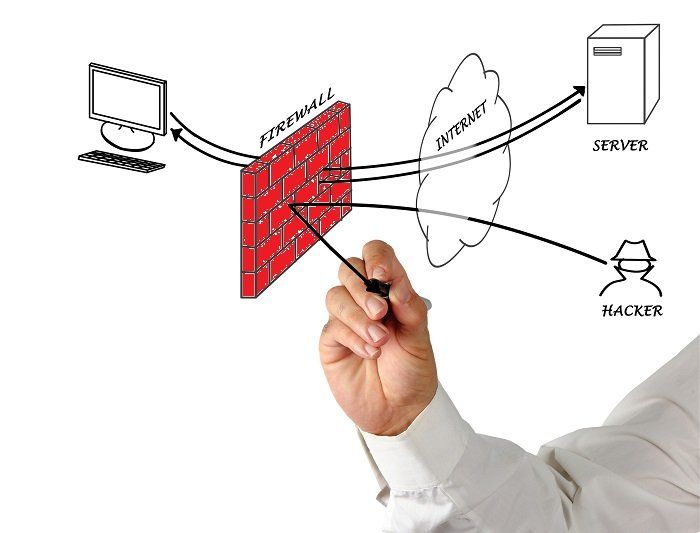
Filtering Types In Firewalls:
Firewalls operate on a specified mode of filtering. They also distinguish themselves by that mode of filtering, they have to operate on. Firewalls are further categorized into 3 filtering mechanisms. These are:
Packet Firewalls:
Packet filtering is based on the
firewall setup. They are configured in such a way that a specified collection
of data is allowed for flowing through the network. Unwanted and useless
packets are dropped by the firewall by allowing only filtered packets filter
into the network.
Proxy Firewalls:
Between an external system and a recipient, the proxy firewalls are acting as a midway. Proxy firewalls let the IP address in a system is hidden from external attacks and provides the required protection.
Inspection Firewalls:
Inspection firewall management is established for inspecting individual packet flowing through the firewall. The decision of either dropping or keep moving a particular packet is based on some specific characteristics of the packet.
The Bottom Line:
Firewalls are performing their operations for a single purpose that is providing protection to a whole network. As networks are of different structures and none of their purposes are common, the different forms and types of firewalls and their dissimilarity of filtration mechanisms are available.





In this advanced era, we can never deny the usefulness and the need of the information security consulting firm. They really are the right ones to be approached, to safeguard a business’s information security matters. For a better security hygiene, you must take this advice seriously, certainly it will pay you off a great deal.